04 CONTROL RISKS
With an advanced intelligent information management system, role-based access permission management reduces the risk of information falling into the wrong hands.
ECM systems are often sought out by organizations to help them comply with certain laws or standards. However, this is just one way that an ECM platform delivers value. The more advanced ECM systems can be used to fulfill the requirements, for instance, of various ISO standards as well as to manage other risk factors in a company. One of those risk factors is security breaches, which can result from a several inefficiencies — like (1) the use of old-school paper documents, or (2) file sharing (or storage) applications that are not ideal for maintaining strict compliance.
In a recent survey from M-Files, respondents were asked, ”How frequently do you store and/or share business documents via a file sync and share application, such as Google Drive, Box, OneDrive or Dropbox?”8
The Problem with Paper Documents
And while it’s true that many organizations could benefit from documented instructions for saving, using and sharing information, vulnerabilities can be significantly diminished by digitizing paper documents and by using ECM systems.
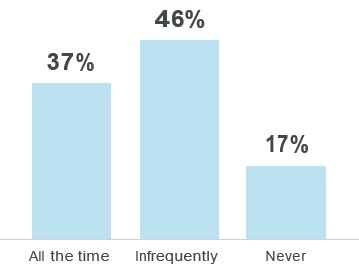
Popular file-sharing services can present security risks, including unauthorized file sharing. But employees often turn to these applications for several reasons — not the least of which is that the tools provided by their companies to enable them to find and share files just aren’t sufficient. With a more advanced intelligent information management system, role-based access permission management, for example, reduces the risk of information falling into the wrong hands. At the same time, continuous developments in data protection legislation also require companies to operate with more precision and have procedures for processing sensitive data. ECM systems can be implemented to fully support these procedures.
There are problems with paper documentation, and there are problems with people using unauthorized, consumer-level file-sharing applications. What they both have in common is that IT departments and compliance departments alike have no visibility or control over where information is being stored and shared. An easy-to-use, intuitive ECM system solves that problem by allowing the IT department to apply permissions and controls more effectively.

Published by M-Files
Focused on information management. Passionate about productivity.
M-Files intelligent information management solutions are disrupting the ECM market, named a Visionary in the Gartner Magic Quadrant for Content Services Platforms. M-Files features a fundamentally new and unique approach that eliminates information silos by providing quick and easy access to the right data and content from any business system and device.
A Commitment to Customer Success
M-Files is a company grown out of one simple vision: that efficiently managing information is a widespread business problem—and that solving this common problem is vital to any business.
Contact Us for more details Tel: 011 568-4900



Recent Comments